Why is hardware more secure than software when implementing critical cryptosystems?
Kimmo Järvinen, co-founder and CTO of Xiphera, explains the underlying differences between hardware and software, and why Xiphera is a firm believer in hardware.
A vast majority of cryptography implementations are software running on general purpose processors. This is totally fine for many applications—and admittedly also the only reasonable option in many cases. But, we at Xiphera believe that software-based cryptography has shortcomings that make it deficient for protecting the most essential systems. The basis for our view is that hardware-based cryptography offers many dvantages both from security and efficiency point-of-views. Here, we take a short look on why we believe hardware (which in our case means primarily field programmable gate arrays, or FPGAs for short) is more secure than traditional software-based cryptography for protecting essential systems, such as industrial control and automation systems or critical communications infrastructure.
Weaknesses of software

When cryptography or other security critical operations are implemented in software, one must implicitly trust a very deep stack of software (cryptographic library, operating system, drivers, compilers, etc.). Security failures in any level may compromise the security offered by a cryptosystem.
After all, software implementations of critical cryptographic omputations are ultimately sharing the same physical resources (CPU, memory, etc.) with other potentially malicious programs.

Despite the many security protections of modern computing systems, if a malicious program succeeds in circumventing even one of such security protections, it can often do serious harm and in the worst case compromise the whole security of a cryptosystem.
Another common source for successful attacks is the fact that in a normal computer system the most sensitive data (for instance, encryption keys) resides in the same memory with non-sensitive data and they may sometimes be exposed even by a trivial bug in a program. Standard examples of such vulnerabilities are the buffer overflow attacks such as the Heartbleed buffer over-read bug in OpenSSL published in 2014 that allowed a remote attacker to read large portions of the victim’s memory that could include passwords, encryption keys, and whatnot.
Software-based cryptographic implementations are also harder to protect against side-channel attacks, which are cryptanalytic attacks that target an implementation of a cryptosystem instead of its mathematical foundations. Side-channel attacks utilize some measurable characteristic of the implementation, such as execution time or instantaneous power consumption, and deduct information about the secret key from these measurements. Protections against side-channel attacks typically require low-level control of operations and operation flows during a cryptographic computation, and such level of control is hard to obtain for software-based implementations, for example, because of microarchitectural optimizations of modern processors.
Finally, even processors may have hardware-level bugs and features that can compromise the security protections of software as demonstrated, for example, by the famous Meltdown and Spectre attacks. Altough such vulnerabilities may be hard to exploit in practice, essential systems should be protected even against them. Unfortunately, processor-level vulnerabilities are extremely hard and expensive to fix for systems already deployed in the field.
Hardware to the rescue

Hardware allows to isolate the critical computations and data into an IP core that is strictly separated from the rest of the system. In particular, cryptographic keys, which are the critical pieces of information for any cryptosystem, can be isolated from the rest of the system into their own memory that can be accessed only by the cryptographic IP cores that require these keys. This is a huge security improvement because it effectively nullifies many of the attacks discussed above. Even if the security of front-end programs or the operating system running on the processor of the main system are comporomised, the attacker still does not have access to the keys. Even if the IP core itself would have a bug that permits a buffer overflow type of an attack, the keys would still remain safe because they are properly isolated inside the IP core. Xiphera offers such isolation of keys, for example, in our TLS 1.3 IP Solution.
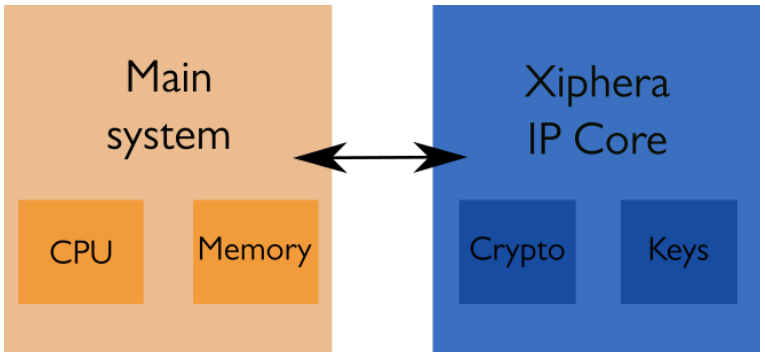
Hardware is also easier to protect against side-channel attacks. Although side-channel attacks are a risk also for hardware-based cryptographic implementations, protections are a lot easier to implement thanks to the level of control that a designer has over the implementation details.
The designer has control literally over individual bits and clock cycles which is often indispendable when designing security-critical implementations. For example, all Xiphera’s IP Cores are fully constant-time (that is to say, that the computation latency does not depend on the secret values) all the way down to the level of a single clock cycle, consequently, nullifying all timing attacks. Implementing a truly constant-time software-based cryptographic implementation can be a suprisingly difficult task, for example, because of many microarchitectural optimization that are out of the programmer’s control.
In addition to the security benefits, hardware-based cryptography also has performance and energy efficiency advantages over software-based implementations. We leave details about these for the future and now simply say that high-performance cryptographic IP cores can reach encryption throughputs of several tens or even hundreds of Gbps and the energy consumed per cryptographic operation is typically only a fraction compared to software running on a general purpose processor.
All the above combined has lead us at Xiphera to think that the most security-critical operations of essential systems, which typically are the cryptographic operations and key management, should be implemented in an isolated manner directly in hardware. FPGAs are close to optimal platforms in this respect because they combine many of the benefits of software and hardware. On the one hand, they can be programmed and updated even in the field after taken into use and, on the other hand, they allow full isolation of security-critical operations and data from the rest of the system as well as full control of the low-level details required for a secure implementation. Besides, FPGAs are already widely used in many industrial control and automation systems, so hardware-based security can be brought into these systems without any additional hardware simply by including Xiphera’s IP Cores and Solutions.
September 28th 2020 : Xiphera
Share on:


